The display dot1x-access-profile configuration command displays the configuration of an 802.1X access profile. Mar 18, 2018 Mobile devices like non-Windows tablets and smart phones are all 'smart' enough to connect to our wireless network with the user only selecting the wifi network and entering their AD credentials.
aaa profile <profile>
authentication-dot1x <dot1x-profile>
authentication-mac <mac-profile>
clone <profile>
devtype-classification
dot1x-default-role <role>
dot1x-server-group <group>
download-role
enforce-dhcp
initial-role <role>
l2-auth-fail-through
mac-default-role <role>
mac-server-group <group>
max-ip ipv4 wireless <max_ipv4_users>
multiple-server-accounting
no ...
open ssid radius accounting
pan-integration
radius-accounting <group>
radius-interim-accounting
rfc-3576-server <ipaddr>
sip-authentication-role <role>
user-derivation-rules <profile>
user-idle-timeout
wired-to-wireless-roam
xml-api-server <ipaddr>
Description
This command configures the authentication for a WLAN.
Syntax
Parameter | Description | Default |
<profile> | Name that identifies this instance of the profile. The name must be 1-63 characters. | “default” |
authentication-dot1x <dot1x-profile> | Name of the 802.1X authentication profile associated with the WLAN. See aaa authentication dot1x. | — |
authentication-mac <mac-profile> | Name of the MAC authentication profile associated with the WLAN. See aaa authentication mac. | — |
clone <profile> | Name of an existing AAA profile configuration from which parameter values are copied. | — |
devtype-classification | The device identification feature can automatically identify different client device types and operating systems by parsing the User-Agent strings in a client’s HTTP packets. When the devtype-classification parameter is enabled, the output of the show user and show user-table commands shows each client’s device type, if that client device can be identified. | enabled |
dot1x-default-role <role> | Configured role assigned to the client after 802.1X authentication. If derivation rules are present, the role assigned to the client through these rules take precedence over the default role. NOTE: This parameter requires the PEFNG license. | guest |
dot1x-server-group <group> | Name of the server group used for 802.1X authentication. See aaa server-group. | — |
enforce-dhcp | When you enable this option, clients must complete a DHCP exchange to obtain an IP address. Best practices are to enable this option, when you use the aaa derivation-rules command to create a rule with the DHCP‑Option rule type. This parameter is disabled by default. | disabled |
| download-role | Enables role download from ClearPass Policy Manager (CPPM) if not defined. | disabled |
initial-role <role> | Role for unauthenticated users. | logon |
l2-auth-fail-through | To select different authentication method if one fails | disabled |
mac-default-role <role> | Configured role assigned to the user when the device is MAC authenticated. If derivation rules are present, the role assigned to the client through these rules take precedence over the default role. NOTE: This parameter requires the PEFNG license. | guest |
mac-server-group group | Name of the server group used for MAC authentication. See aaa server-group. | — |
max-ip ipv4 wireless <max_ipv4_users> | Control the number of IPv4 addresses that can be associated to single wireless user. Range: 1-32 WARNING: Increasing the max-ip limit may prevent the system from scaling to maximum users on all master/local controllers. For more information, refer to Usage Guidelines for max-ip ipv4 wireless. | 2 |
| multiple-server-accounting | If enabled, the controller sends RADIUS accounting to all servers in RADIUS accounting server group. | disabled |
no | Negates any configured parameter. | — |
open ssid radius accounting | Initiates RADIUS accounting as soon as the user associates to an Open SSID without any authentication. NOTE: Do not enable this parameter for wired users. If enabled, the controller sends RADIUS accounting packets for unauthenticated wired users. | disabled |
| pan-integration | The profile requires mapping at a Palo Alto Networks (PAN) firewall | disabled |
radius-accounting <group> | Name of the server group used for RADIUS accounting. See aaa server-group. | — |
radius-interim-accounting | By default, the RADIUS accounting feature sends only start and stop messages to the RADIUS accounting server. Issue the interim-radius-accounting command to allow the controller to send Interim-Update messages with current user statistics to the server at regular intervals. | disabled |
rfc-3576-server <ip-addr> | IP address of a RADIUS server that can send user disconnect NOTE: This parameter requires the PEFNG license. | — |
sip-authentication-role <role> | Configured role assigned to a session initiation protocol (SIP) client upon registration. NOTE: This parameter requires the PEFNG license. | guest |
user-derivation-rules <profile> | User attribute profile from which the user role or VLAN is derived. | — |
user-idle-timeout | The user idle timeout for this profile. Specify the idle timeout value for the client in seconds. | disabled |
wired-to-wireless-roam | Keeps user authenticated when roaming from the wired side of the network. | enabled |
xml-api-server <ip-addr> | IP address of a configured XML API server. See aaa xml-api. NOTE: This parameter requires the PEFNG license. | — |
Usage Guidelines
The AAA profile defines the user role for unauthenticated users, the default user role for MAC or 802.1X authentication, and user derivation rules. The AAA profile contains the authentication profile and authentication server group.
There are predefined AAA profiles available, default-dot1x, default-mac-auth, and default-open. These profiles have the parameter values shown in the following table.
Parameter | default-dot1x | default-mac-auth | default-open |
authentication-dot1x | default | N/A | N/A |
authentication-mac | N/A | default | N/A |
dot1x-default-role | authenticated | guest | guest |
dot1x-server-group | N/A | N/A | N/A |
initial-role | logon | logon | logon |
mac-default-role | guest | authenticated | guest |
mac-server-group | default | default | default |
radius-accounting | N/A | N/A | N/A |
rfc-3576-server | N/A | N/A | N/A |
user-derivation-rules | N/A | N/A | N/A |
wired-to-wireless roam | enabled | enabled | enabled |
Usage Guidelines for max-ip ipv4 wireless
Changing the max-ip ipv4 wireless parameter from the default value is recommended for special deployments. If your WLAN has multiple device IP associated to single MAC address, you can increase the this value from the default value of 2.
The default value is 2 IPv4 users per wireless user. Total number of IPv4 users created can be a maximum of two times the license. If you configure 32 max-ip IPv4 users , total number of IPv4 users is 32 times the license. This can prevent the controller from scaling to the maximum limit of IP users. Total number of IPv4 users should be scaled down to offset this issue.

Increasing the value of the max-ip ipv4 wireless parameter may increase the look-up time due to an increase in the creation and deletion of IPv4 users on the controller. In a deployment where there is Captive Portal and 802.1X authentication implemented, increasing the number of IPv4 users can further deplete performance.
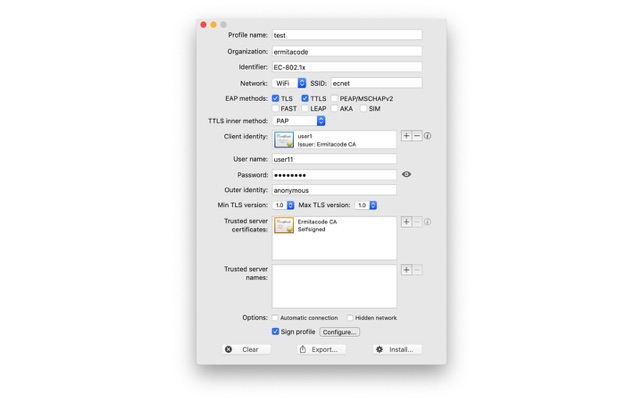
Dot1x Credentials Profile
Example
The following command configures an AAA profile that assigns the “employee” role to clients after they are authenticated using the 802.1X server group “radiusnet”.
aaa profile corpnet
dot1x-default-role employee
dot1x-server-group radiusnet
Command History
Version | Description |
ArubaOS 3.0 | Command introduced. |
ArubaOS 3.4.1 | License requirements changed in ArubaOS 3.4.1, so the sip-authentication-role parameter required the Policy Enforcement Firewall license instead of the Voice Services Module license required in earlier versions. |
ArubaOS 6.1 | The radius-interim-accounting, devtype-classification and enforce-dhcp parameters were introduced. |
ArubaOS 6.3 | The user-idle-timeout parameter was introduced. |
ArubaOS 6.4 | The multiple-server-accounting and download-role parameters were introduced. |
ArubaOS 6.4.1.0 | The user-idle-timeout parameter now accepts a value of 0. |
ArubaOS 6.4.3.0 | The max-ip and open ssid radius accounting parameters were introduced. |
Command Information
Platforms | Licensing | Command Mode |
All platforms | Base operating system, except for noted parameters | Config mode on master controllers |
Dot1x Profile Login
